Security experts have long advised people to avoid using public
WiFi networks because of the risk of being hacked.
Despite
those warnings, free WiFi is becoming more widespread and popular, with
consumers browsing the web courtesy of local governments, cable companies,
neighborhood coffee shops, and others that offer an on-the-house hot spot.
Along with convenience for the public, public
Wi-Fi hotspots can also provide an easy way for identity thieves and
cybercriminals to monitor what you’re doing online and to steal your passwords,
your personal information, or both. Never assume that a public Wi-Fi network is
safe or secure. Remember, these passwords are shared, so anyone nearby can
easily hop onto the network and see what you’re doing. The most used
attack is MITM that very easily get your data .Lets know about this attack-
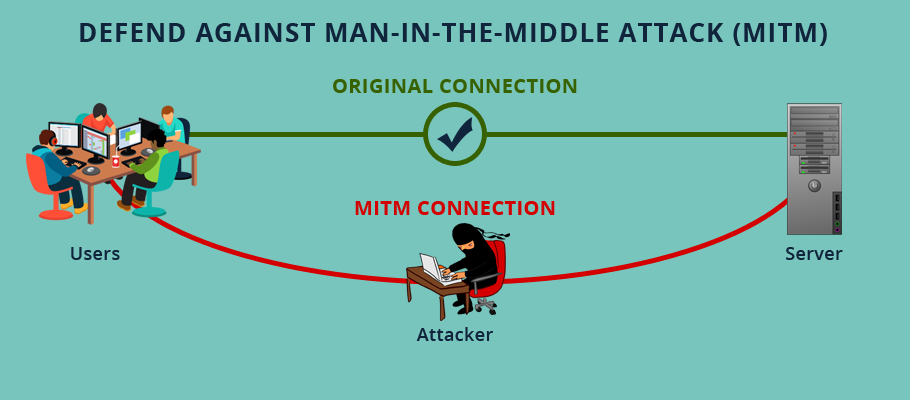
What is MITM attack
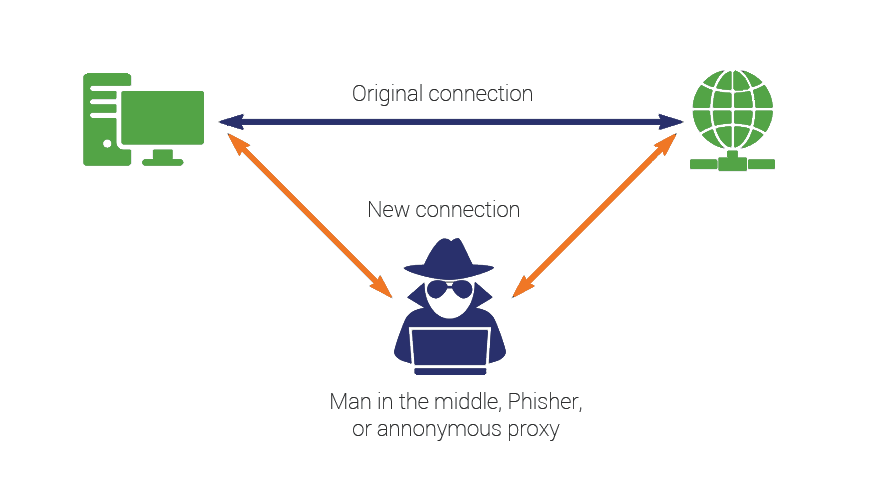
A man in the middle (MITM) attack is a
general term for when a perpetrator positions himself in a conversation between
a user and an application—either to eavesdrop or to impersonate one of the
parties, making it appear as if a normal exchange of information is underway.
The goal of an attack is to steal personal
information, such as login credentials, account details and credit card
numbers. Targets are typically the users of financial applications, SaaS
businesses, e-commerce sites and other websites where logging in is required.
Information obtained during an attack could
be used for many purposes, including identity theft, unapproved fund transfers
or an illicit password change..
Broadly speaking, a MITM attack is the equivalent of a mailman opening your bank statement, writing down your account details and then resealing the envelope and delivering it to your door.
Man in the middle attack example
MITM attack progression
Successful MITM execution has two distinct
phases: interception and decryption.
Interception
The first step intercepts user traffic
through the attacker’s network before it reaches its intended destination.
The most common (and simplest) way of doing
this is a passive attack in which an attacker makes free, malicious WiFi
hotspots available to the public. Typically named in a way that corresponds to
their location, they aren’t password protected. Once a victim connects to such
a hotspot, the attacker gains full visibility to any online data exchange.
Attackers wishing to take a more active
approach to interception may launch one of the following attacks:
·
IP spoofing involves an attacker disguising himself as an application by
altering packet headers in an IP address. As a result, users attempting to
access a URL connected to the application are sent to the attacker’s website.
·
ARP spoofing is the process of linking an attacker’s MAC address with the IP
address of a legitimate user on a local area network using fake ARP messages.
As a result, data sent by the user to the host IP address is instead
transmitted to the attacker.
·
DNS spoofing, also known as DNS cache poisoning, involves infiltrating a DNS server
and altering a website’s address record. As a result, users attempting to
access the site are sent by the altered DNS record to the attacker’s site.
Decryption
After interception, any two-way SSL traffic
needs to be decrypted without alerting the user or application. A number of
methods exist to achieve this:
·
HTTPS spoofing sends a phony certificate to the victim’s browser once the
initial connection request to a secure site is made. It holds a digital
thumbprint associated with the compromised application, which the browser
verifies according to an existing list of trusted sites. The attacker is then
able to access any data entered by the victim before it’s passed to the
application.
·
SSL BEAST (browser exploit against SSL/TLS) targets a TLS version 1.0
vulnerability in SSL. Here, the victim’s computer is infected with malicious
JavaScript that intercepts encrypted cookies sent by a web application. Then
the app’s cipher block chaining (CBC) is compromised so as to decrypt its
cookies and authentication tokens.
·
SSL hijacking occurs when an attacker passes forged authentication keys to both
the user and application during a TCP handshake. This sets up what appears to
be a secure connection when, in fact, the man in the middle controls the entire
session.
·
SSL stripping downgrades a HTTPS connection to HTTP by intercepting the TLS
authentication sent from the application to the user. The attacker sends an
unencrypted version of the application’s site to the user while maintaining the
secured session with the application. Meanwhile, the user’s entire session is
visible to the attacker.
Man in the middle attack prevention
Blocking MITM attacks requires several
practical steps on the part of users, as well as a combination of encryption
and verification methods for applications.
For users, this means:
·
Avoiding WiFi connections that aren’t
password protected.
·
Paying attention to browser notifications
reporting a website as being unsecured.
·
Immediately logging out of a secure
application when it’s not in use.
·
Not using public networks (e.g., coffee
shops, hotels) when conducting sensitive transactions.
For website operators, secure communication
protocols, including TLS and HTTPS, help mitigate spoofing attacks by robustly
encrypting and authenticating transmitted data. Doing so prevents the
interception of site traffic and blocks the decryption of sensitive data, such
as authentication tokens.
It is considered best practice for
applications to use SSL/TLS to secure every page of their site and not just the
pages that require users to log in. Doing so helps decreases the chance of an
attacker stealing session cookies from a user browsing on an unsecured section
of a website while logged in.’
Hope you understand . lest talk about encryption.
Does
Encryption Protect You?
One of the biggest game changers in WiFi safety
is the now widespread use of encryption. Transport layer security, or TLS, is
used to encrypt data sent between your browser and the servers it’s trying to
access. It’s signified with an “HTTPS” in a web address, as well as a little
padlock logo.
TLS scrambles the data, leaving it all but useless
to any attacker who might intercept it, including hackers who can carry out
“man in the middle” attacks by using the same WiFi network their target is
using.
Encryption was once reserved for banking sites
and others that routinely traffic personal information. But now it's standard
on just about every major website, including Amazon, Google, and Wikipedia.
According to Mozilla, about 87 percent of
the web traffic to U.S. users of its Firefox browser is now encrypted. That’s
up from about 73 percent in January of this year and 56 percent a year before
that. That's the good news.
But experts warn that TLS encryption isn’t
perfect. It can be broken by sophisticated hackers.
“Even HTTPS can be hijacked and downgraded,”
says Clay Miller, chief technology officer for SyncDog, which focuses on mobile
security. “Meanwhile, a lot of files, PDFs, medical records, and bank
statements still aren’t encrypted.”
A recent study by researchers in Italy and Austria found
that about 5.5 percent of the top 10,000 websites secured by HTTPS had TLS
security flaws that could make them vulnerable to man-in-the-middle attacks or
allow an attacker to at least partly decrypt them.
In addition, while you can look for the trusty
padlock if you're on a laptop or desktop computer, that isn’t as easy on a mobile device, especially when you're using
apps that don’t show web addresses at all.
For this reason, even Wisniewski agrees that
when using phone apps, it’s better to play it safe and rely on the phone’s
cellular data connection, which is generally much more secure than an unsecured
WiFi hot spot.
Are
Municipal Hot Spots Safer?
Many people might be wary of WiFi at their
favorite neighborhood haunts but feel more comfortable jumping on a connection
provided by their city or their cable company. Website encryption aside, don't
those big, professionally managed networks have their own security measures in
place?
Some do. But municipal and corporate WiFi
networks are not all created equal, and consumers should do their homework
before going online.
For example, New York City operates two WiFi networks:
an open network that doesn’t offer any protection, forcing you to rely on
website encryption or protection built into your device, and a private network
that encrypts all of the traffic that passes through it.
Both are free to the public, and all that’s needed to register
is an email address. The encrypted network also requires you to download a
digital security key, and it currently can be accessed only from Apple mobile
devices.
The city encourages anyone using the unsecured
network to stick with encrypted websites and avoid any sensitive activities
such as banking or credit card transactions.
The situation is similar with Optimum, a division of Altice USA that
provides cable and internet services, including a large network of WiFi hot
spots in the New York tri-state area. The company says that it encrypts
customers' log-in information when they sign on to its hot spots but that
they're largely on their own after that while browsing the web.
Optimum encourages users to make sure their
firewalls and antivirus software are up to date, and it offers a free
security suite that includes those elements.
Are
You Really a Target?
Like a lot of security-related decisions,
deciding whether or not to use public WiFi comes down to judging the trade-off
between security and convenience. It’s up to you to decide whether the benefits
are worth the risks.
If you’re a government official with state
secrets on your phone or an executive for a Fortune 500 company with plans for
your next great product on your laptop, the decision to stay off public WiFi is
an easy one, Wisniewski says.
But for ordinary people, most have only a
certain amount of patience and effort to spend when it comes to staying safe
online. Wisniewski thinks that effort would probably be better spent locking
down their accounts with better passwords and two-factor authentication.
“What would be lost if you got man-in-the-middled
at Starbucks?” he asks. “Will I log on to my bank account at Starbucks? No. But
will I log on to Twitter? Sure.”
But Davis counters that even if the odds of
someone getting hacked are extremely remote, letting go of good habits is a bad
idea.
“We, as security professionals, need to think
about how best we can keep consumers informed and educated,” he says. “To say
they don’t need to worry about public WiFi anymore probably sends the wrong
message.”
The bottom line: Public WiFi is safer now, but
it's not entirely safe. That's especially true if you're using mobile apps,
where there's often no way to tell whether data is being encrypted.
How
Can You Stay Safe?
Here are a few tips for staying safe online,
especially if you’re using a public WiFi connection.
Use strong passwords. Wisniewski says bad passwords are his No.
1 security pet peeve. Long strings of random characters are best, and don’t be
tempted to use the same password for multiple accounts. Credential-stuffing
attacks, where hackers use armies of bots to run lists of previously stolen
passwords against other accounts, are on the rise.
Enable two-factor authentication (2FA). Requiring a second element for logging on to a website, such a
passcode texted to your phone or a physical key you insert into your computer,
goes a long way toward keeping hackers out even if your password is
compromised.
Be careful what you post. Social media accounts can be a virtual
gold mine for hackers looking to crack your passwords. Be careful about posting
too many personal details.
Consider using a VPN. Virtual private networks encrypt all the data traveling
back and forth from your device. Miller says they’re great protection against
man-in-the-middle attacks. But not all security experts agree. Wisniewski
thinks that they’re unnecessary and that many are too awkward for most
consumers to use.
Encrypt your devices. A VPN and TLS security protect your data
in transit, but Miller says you need to make sure that what's stored on your
device is secure, too. That way, if someone gains access to your device, your
data will remain scrambled. With smartphones, doing this is as simple as
setting up a passcode. But encrypting laptops can take a bit more work.
Beware of phishing. Emails that appear to be from your bank or
credit card company could actually be from a hacker trying to gain access to
your account. Clicking on a link in one of those emails could send you to a
fake website designed to steal your log-in credentials or result in malware or
spyware being installed on your device. You're better off just typing the URL
of the financial institution directly into your browser.
Delete old information. There’s no reason to keep copies of
three-year-old tax returns saved on your work laptop or mobile device. Personal
documents are better backed up at home. And regularly deleting documents you
don’t need anymore reduces what hackers can steal, Miller says.


0 Comments
If you have any dought, please comment bellow.